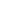Data breaches cost organizations an average of $4.88 million per incident according to IBM's data breach report, yet most privacy breaches stem from preventable mistakes. This comprehensive guide reveals the most expensive data privacy errors affecting business owners, startup founders, developers, and researchers:
- Most Common Costly Mistakes: Inadequate access controls, poor vendor risk management, and insufficient employee training create 70% of data privacy vulnerabilities
- Hidden Costs Beyond Fines: Customer trust erosion, reputational repair, and operational disruption often exceed regulatory penalties by 300-500%
- Critical Implementation Gaps: Organizations frequently choose inappropriate cybersecurity solutions and fail to implement continuous monitoring systems
- Compliance Pitfalls: Misunderstanding industry-specific requirements (GDPR, CCPA, HIPAA, PCI DSS) leads to expensive regulatory violations
- Competitive Advantage: Proper data classification, incident response planning, and comprehensive security frameworks transform weaknesses into business strengths
Understanding Data Security Fundamentals and Why Mistakes Happen
What is Data Security and Why It Matters for Your Business
Data security means protecting personal, customer, and confidential information. Organizations use measures to stop unauthorized access, cybercrime, and data breaches. In today's digital world, good data privacy and security strategies protect more than just information. They keep customer trust, follow laws, and help companies stay competitive.
Modern businesses handle vast amounts of personal identifiable information (PII), including:
- Customer Information: Personal data, payment details, contact records, and transaction histories
- Employee Data: Recruitment records, performance evaluations, personal references, and confidential HR information
- Healthcare Records: Protected health information requiring HIPAA compliance and specialized encryption measures
- Financial Data: Payment processing information subject to PCI DSS requirements and fraud prevention protocols
Key data protection laws establish strict compliance requirements:
- GDPR (General Data Protection Regulation): Applies to EU personal data with penalties up to 4% of global revenue
- CCPA (California Consumer Privacy Act): Governs California residents' privacy rights with significant financial penalties
- HIPAA: Protects healthcare information with criminal penalties and mandatory breach notifications
- PCI DSS: Secures payment card data through comprehensive technical and operational requirements
The Hidden Costs of Data Privacy Mistakes Beyond Financial Penalties
While regulatory fines grab headlines, the true cost of data privacy negligence extends far beyond immediate financial penalties. Privacy breaches trigger multiple consequences:
Financial Impact:
- Direct regulatory fines and penalties
- Legal fees and litigation costs
- Forensic investigation expenses
- Credit monitoring services for affected customers
- Cyber insurance premium increases
Operational actions have consequences.
- System downtime and productivity losses
- Emergency security implementations
- Additional compliance auditing requirements
- Enhanced monitoring and reporting obligations
Long-term Business Impact:
- Customer acquisition cost increases of 25-40%
- Revenue decline from customer churn
- Competitive disadvantage in privacy-conscious markets
- Difficulty attracting top talent concerned about employer reputation
Why Even Cybersecurity-Aware Companies Make Critical Errors
Cybercriminals keep changing their tactics. Even well-prepared organizations can be vulnerable to social engineering, phishing, and advanced persistent threats. Common vulnerabilities include several types of security weaknesses.
Technology Gaps:
- Over-reliance on perimeter security (firewalls, antivirus) without comprehensive data protection
- Inadequate intrusion detection systems that miss sophisticated attacks
- Outdated security patches and vulnerability management processes
Human Factors:
- Insufficient security awareness training on current threat landscapes
- Lack of regular updates on evolving social engineering tactics
- Missing training on data subject rights and privacy regulations
- Poor understanding of legitimate interest and data minimization principles
Challenges Organizations Face:
- Navigating complex regulatory frameworks across diverse jurisdictions.
- Striking a balance between operational efficiency and robust privacy protection.
- Managing with limited resources for thorough risk assessments and security audits.
The Most Expensive Data Classification and Handling Mistakes
Failing to Properly Identify and Classify Sensitive Information
Data mapping is the base of good data privacy management. However, many organizations do not fully see their information assets. There are important classification categories.
Data Sensitivity Levels:
- Public information requiring minimal protection
- Internal data needing basic access controls
- Confidential information requiring encryption and monitoring
- Highly sensitive personal data demanding comprehensive security measures
Different industries have specific requirements.
- Healthcare organizations: Protected health information under HIPAA compliance
- Financial institutions: Payment data security following PCI DSS standards
- EU-based companies: GDPR personal data protection requirements
- Research institutions: Academic data and intellectual property protection
Inadequate Access Controls and Permission Management
Role-based access control failures create significant vulnerabilities in data protection frameworks. Common implementation mistakes include:
Permission Management Errors:
- Granting excessive permissions that violate data minimization principles
- Failing to implement least-privilege access controls
- Inadequate review processes for user access rights
- Missing access controls for contractors and temporary workers
There are weaknesses in authentication.
- Inconsistent multi-factor authentication implementation across systems
- Weak password policies that don't address modern threat landscapes
- Inadequate two-factor authentication for administrative accounts
- Missing authentication requirements for API access and system integrations
Mobile and Remote Access Challenges:
- Insufficient Mobile Device Management for remote workers
- Weak controls for personal devices accessing confidential information
- Inadequate VPN security and monitoring capabilities
- Missing encryption requirements for mobile data storage
Poor Data Retention and Disposal Practices
Asset disposal mistakes create lasting vulnerabilities long after data should have been destroyed. Key challenges include:
Data Retention Policy Failures:
- Unclear retention periods for different data categories
- Excessive accumulation of personal information increasing breach exposure
- Inconsistent policies across departments and business units
- Missing procedures for legal hold and litigation requirements
Secure Disposal Requirements:
- Inadequate encryption methods that don't render data completely unrecoverable
- Improper destruction of physical media and backup systems
- Missing verification procedures for data destruction completion
- Inadequate disposal of cloud-stored data and system backups
Third-Party Vendor Complications:
- Vendor contracts lacking appropriate data disposal requirements
- Missing audit capabilities to verify proper vendor data handling
- Inadequate oversight of subcontractor data destruction processes
- Unclear data ownership and disposal responsibilities throughout service relationships
Critical IT Security Risk Management Oversights
Neglecting Cloud Data Protection in Multi-Cloud Environments
Cloud computing adoption creates new security challenges that traditional IT security approaches cannot adequately address. Multi-cloud environments need special data protection strategies. These strategies must consider different security models, compliance rules, and vendor abilities.
API Security becomes critical as organizations integrate various cloud services and applications. Weak API implementations create entry points for unauthorized access that can compromise entire data ecosystems. Organizations must use full API security systems. These systems include authentication, authorization, and continuous monitoring.
Cloud storage systems often default to configurations that prioritize accessibility over security. Organizations must actively set up encryption, access controls, and monitoring systems. This ensures they protect confidential information stored in cloud environments.
Insufficient Employee Training and Security Awareness Programs
Human error remains the leading cause of data breaches, yet many organizations underinvest in comprehensive employee training programs. Essential training components include:
Current Threat Education:
- Recognition of sophisticated phishing attacks and social engineering tactics
- Understanding of insider threat scenarios and warning signs
- Awareness of ransomware and malware protection strategies
- Knowledge of credential theft prevention and password security
Privacy Rights and Procedures:
- Data subject rights under GDPR, CCPA, and other privacy laws
- Proper handling of DSARs (Data Subject Access Requests)
- Understanding of consent requirements and privacy notice obligations
- Knowledge of data minimization principles and legitimate interest assessments
Different roles need specific training.
- HR departments handling candidate data and interview notes during recruitment
- Finance teams processing payment data and financial records
- IT staff managing system access and security configurations
- Customer service representatives accessing personal information for support
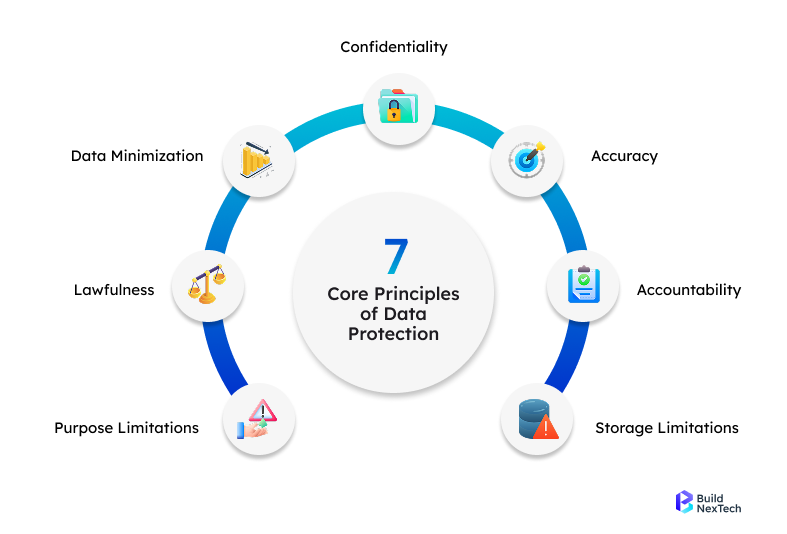
Weak Incident Response and Data Breach Protection Plans
Many organizations do not have complete Data Breach Response Plans. These plans should cover both technical fixes and legal notification rules. Critical planning elements include:
Incident Response Team Structure:
- Pre-established breach response team with clear roles and responsibilities
- Designated Data Protection Officer with appropriate authority and resources
- Cross-functional coordination between IT, legal, communications, and executive leadership
- External specialist contacts for forensic investigation and legal counsel
Response Procedures:
- Immediate containment protocols to limit breach scope and impact
- Evidence preservation requirements for regulatory investigations
- Breach notification timelines for customers, regulators, and law enforcement
- Communication templates for internal and external stakeholder updates
Organizations should assess their preparedness.
- Regular penetration testing and vulnerability scanning to identify weaknesses
- Tabletop exercises simulating various breach scenarios and response procedures
- Security audits evaluating incident response capabilities and team readiness
- Continuous improvement processes incorporating lessons learned from incidents and industry best practices
Technology Implementation Mistakes That Compromise Security
Even with strong policies in place, technology gaps can create vulnerabilities that cybercriminals exploit. Misaligned tools, outdated monitoring methods, or weak recovery plans often leave organizations exposed. Below are some of the most common mistakes that compromise data protection and overall security posture.
Choosing Inadequate Cybersecurity Solutions for Your Business Size
Small and medium organizations often use cybersecurity solutions made for large companies. This creates complexity and lowers effectiveness. Alternatively, they may choose inadequate tools that cannot scale with business growth or address evolving security threats.
Cost considerations cannot drive cybersecurity decisions without considering potential data breach costs. Industry research shows that the average cost of a data breach is much higher than usual cybersecurity spending. This makes full protection a smart business investment, not just an expense.
Cybersecurity certifications help organizations choose the right solutions. Organizations must know which standards fit their industry and needs. ISO 27001, SOC 2, and NIST frameworks offer comprehensive guidance for establishing appropriate security controls.
Failing to Implement Continuous Data Protection and Monitoring
Real-time monitoring systems enable organizations to detect security events before they escalate into major breaches. However, many organizations rely on periodic assessments that cannot identify rapidly evolving threats or insider threat activities.
Event tracking must go beyond network monitoring. It should include user behavior analysis, data access patterns, and unusual activities that may show unauthorized access attempts. This requires sophisticated Analytics Tools that can process large volumes of data while identifying subtle indicators of compromise.
Malware protection requires continuous updates and behavioral analysis capabilities that can identify zero-day threats and advanced persistent threats. Traditional signature-based antivirus software cannot protect well against advanced attacks by modern cybercriminals.
Inadequate Backup and Recovery Planning for Sensitive Data
Ransomware attacks target backup systems. Because of this, traditional backup strategies do not provide full data protection. Organizations must use backup solutions that cannot be changed and offline storage. These must stay available during major security incidents.
Recovery planning must address both technical restoration and regulatory compliance requirements. Data breach rules require organizations to restore operations quickly. They must also keep evidence for investigations and forensic analysis.
Tokenization adds protection for sensitive data in backup systems. It makes sure that even if backups are compromised, actual personal or confidential data is not exposed. This approach particularly benefits organizations handling payment data or protected health information.
Avoiding Compliance Pitfalls and Regulatory Mistakes
Misunderstanding Industry-Specific Data Protection Requirements
Healthcare organizations must navigate HIPAA requirements that extend beyond general data privacy regulations. Protected health information needs special technical, administrative, and physical security measures. These differ a lot from standard cybersecurity methods.
Financial services face PCI DSS obligations for payment data processing, while also addressing consumer privacy rights under various state and federal regulations. The complexity of overlapping requirements creates compliance challenges that require specialized legal and technical expertise.
Privacy laws continue evolving, with new regulations emerging at state, federal, and international levels. Organizations must set up monitoring systems for regulatory changes. They also need assessment processes to check how these changes affect their operations.
Inadequate Vendor and Third-Party Risk Management
Supply chain management creates complex data protection challenges as organizations share personal information with numerous third-party vendors. Each vendor relationship represents a potential vulnerability that requires comprehensive risk assessment and ongoing monitoring.
Vendor contracts must include clear data protection rules, liability details, and audit rights. These let organizations check if vendors follow privacy laws. Standard vendor agreements often lack adequate privacy protection clauses that address current regulatory requirements.
Security assessments of third-party vendors must check both their technical skills and their company practices. Organizations check vendor staff training. They also check security awareness programs. They check incident response abilities. These factors can affect how well data is protected.
Poor Documentation and Audit Trail Management
Privacy audits need full documentation. This documentation must show compliance with relevant regulations and internal policies. Organizations often find it hard to provide enough records during regulatory investigations or when customers ask about data handling.
Criminal record data, personal references, and other sensitive job information need special documentation procedures. These procedures must protect privacy and meet legitimate business needs. HR departments must keep operations efficient. They also need to keep complete records.
Data mapping documentation must remain current as business operations evolve. Outdated records cannot support effective privacy protection. They also cannot help with regulatory compliance. Therefore, organizations must update documentation continuously to keep protection measures adequate.
BuildNexTech's Commitment to Enterprise Data Security and Confidentiality
BuildNexTech recognizes that modern businesses require comprehensive data privacy solutions that address both current threats and evolving regulatory requirements. Our approach uses technical skills and business knowledge. We provide practical security solutions that protect customer trust and support efficient operations.
Our team includes privacy professionals, cybersecurity experts, and compliance specialists who understand the complex challenges facing business owners, startup founders, developers, and researchers. We provide consulting IT security services that address specific industry requirements while implementing scalable solutions that grow with your business.
Data Privacy Week initiatives and ongoing security awareness programs help organizations maintain current knowledge of emerging threats and regulatory changes. BuildNexTech's commitment extends beyond initial implementation to provide continuous support for evolving data protection requirements.
Conclusion: Turn Data Security Weaknesses Into Competitive Advantages Before Costly Mistakes Strike
BuildNexTech recognizes that modern businesses require enterprise data security and data privacy solutions that address both current cybersecurity threats and evolving compliance requirements. Our approach combines advanced IT security services with deep business knowledge to deliver practical solutions that protect customer trust and ensure operational efficiency.
Our team includes privacy compliance specialists, cybersecurity consultants, and industry-certified experts who understand the complex challenges faced by business owners, startup founders, developers, and researchers. We deliver consulting IT security services tailored to specific industry needs while implementing scalable security solutions that grow with your business.
Through security awareness programs and initiatives such as Data Privacy Week, we help organizations stay ahead of emerging threats, meet regulatory compliance standards, and maintain robust data protection practices. BuildNexTech’s commitment extends beyond initial implementation, offering ongoing support for evolving data protection requirements.
People Also Ask
What cybersecurity certifications are most valuable for data protection roles?
Most valuable certifications – CISSP, CISM, CISA, CEH, and ISO/IEC 27001 Lead Implementer are highly regarded for data protection roles.
How much should a company budget for comprehensive data security management?
Allocate about 7–10% of the total IT budget for comprehensive data security management.
What's the difference between consulting its security services and managing security services?
Consulting provides one-time expert advice; managed services deliver ongoing, outsourced security operations and monitoring.
How often should companies update their data security management system?
Review and update the data security management system annually or after major tech/regulatory changes.





















.webp)
.webp)
.webp)