That cloud icon has become second nature - whether you’re putting vacation pictures into Google Drive, in a co-authoring meeting on a business report in Microsoft 365, or streaming your favorite show on Netflix. The cloud is responsible for almost every digital transaction these days.
While it is certainly convenient, there is one question we need to ask: while a cloud is convenient, is it safe? Convenience is certainly hard to argue against. The issue with the cloud is that there are many threats to your confidentiality, availability, and integrity of data. Everyone knows there exists the risk of data breaches, leaks, and even possible misconfigurations.
This guide is designed for IT leaders, developers, and everyday users to help navigate the clouds of confusion from cloudy computing. We will make sure you leave empowered. We will discuss the most critical cloud security tips and practices, and the biggest threats out there, along with tools to help secure your data. You will leave with identified steps you can use to help protect your data and establish a proper cloud computing defense posture.
Let’s get into it.
💡 What will you get from this blog?
📌 Why does cloud security matter in 2025?
📌 Vulnerabilities and common threats
📌 12 Cloud security tips
📌 Tools and strategies enterprises use to secure data
Why Cloud Security Matters More in 2025
Cloud computing has become a cornerstone of digital transformation. However, higher levels of adoption bring higher levels of risk. Organizations must now operate within an environment where there are consequences every day, and malicious actors can launch real-time attacks using AI.
- AI-based cyber threats targeting the cloud : Threat actors are frequently utilizing automated technologies or AI/ML solutions to perform sophisticated phishing attempts, inject bad traffic, or breach data without permission. Traditional defenses are no longer effective.
- Regulatory pressures from legislation: Global regulations like GDPR, HIPAA, PCI DSS, etc. have all led to global legislation around protecting personal data. Organizations have to worry about non-compliance, which could lead to fines and reputational damage to their organization.
- Multi-cloud and hybrid cloud complexity: Given the multi cloud or hybrid cloud world we live in today, organizations operate workloads in AWS, Azure, Google Cloud, Security etc. The greater the number of clouds that you are using to serve workloads, the greater the chances for errors/misconfigurations, like failing to restrict public access to a cloud storage bucket if you do not have posture management to identify potential security risks.
Cloud security best practices safeguard sensitive information types by addressing potential threats. Strong authorization mechanisms and proactive data protection measures ensure organizations remain resilient against evolving cyber risks in today’s digital landscape.
Understanding Cloud Infrastructure: IaaS, PaaS, SaaS
Before diving into security practices, it’s important to understand the three main cloud service models.
Threats and Damages Without Cloud Security
The absence of adequate cloud security tips makes cloud environments more susceptible to highly negative risks to their operations and reputation.
Unauthorized access to sensitive data - Poor access management can lead to needed stolen credentials and unauthorized access to sensitive data types, like financial data or healthcare data.
Data breaches and regulatory fines - In the absence of compliance to frameworks like PCI DSS or ISO 27001, organizations run the risk of data breaches and can incur large fines and litigation claims resulting from data breaches.
DDoS attacks and service downtime - Malicious actors can attack through DDoS techniques at cloud services and take down services altogether or impact loss of + service availability impacting revenue.
Loss of customer trust - All compromised sensitive data or workloads cause the business to lose customer trust and ultimately revenue loss by affecting future customers.
Operational disruption - Without an incident response plan in place and vulnerability management in place and active, organizations run a risk of outages and failure of service delivery.
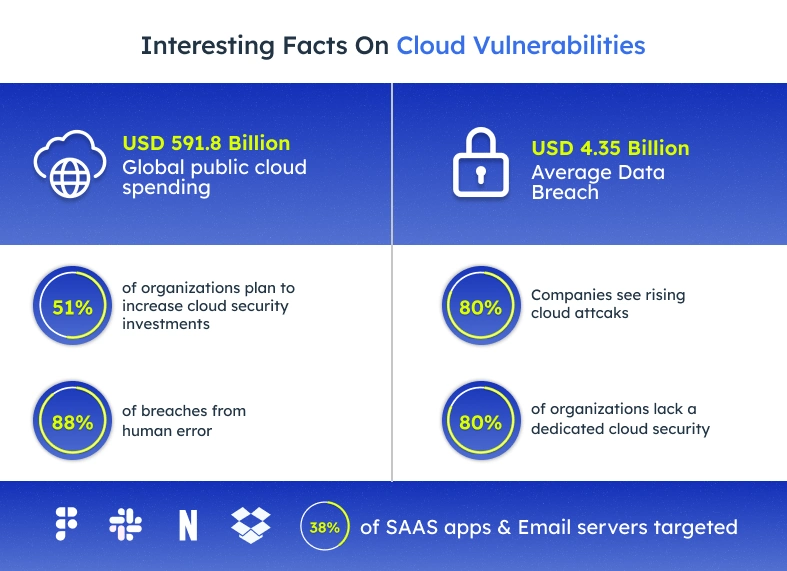
Key Cloud Security Tips for 2025
Every business should follow important steps to keep cloud systems safe. They must stop unauthorized access. They should protect sensitive data. Here are 12 cloud security tips that every user must follow.
Use multi-factor authentication everywhere
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring more than just a password. Even if a password is stolen, attackers cannot log in without the second factor (such as a code, mobile app, or biometric).
- Prevents unauthorized access to accounts
- Strengthens weak or reused passwords
- Works across all major cloud service providers

Follow the principle of least privilege
This means only giving users and services the permissions they need - nothing more. Restrictions on access will limit damage if misfortune struck and an account was hacked.
- Manage access tightly
- Use strong authentication practices
- Verify user role and privileges regularly
Encrypt data in transit and at rest
Encryption ensures that even if attackers steal or intercept files your storage, they will not be able to read the files.
- Utilize Azure Storage Service Encryption, Azure Managed Disks, and Azure SQL Database in the Microsoft Cloud
- Encrypt sensitive data at rest in storage buckets or whenever it is in transit
- Protect sensitive information and observe regulatory compliance, such as PCI DSS and ISO 27001.
Ensure cloud configurations are not misconfigured
I read a study in a report from SentinelOne titled "50+ Cloud Security Statistics in 2025" that said 23% of cloud security incidents occur because of cloud misconfigurations. Cloud Security Posture Management (CSPM) tools will automatically scan your settings and correct misconfigurations before they are exploited by hackers.
- Detecting public access of storage or servers
- Flag non-compliance deviations
- Maintaining security controls properly in cloud services
Continuously monitor accounts and workloads
Cloud threats do not always occur during your working hours -- you must always have continuous monitoring.
- Detect suspicious activities as they occur
- Block malicious traffic before damage occurs
- Implement integrated platforms - For example, Microsoft Sentinel or Google Cloud Security.
Secure APIs and microservices against misuse
Modern applications are built largely on APIs and microservices which can be abused if unsecured.
- Utilize API gateways and container security
- Enforce authentication mechanisms for APIs
- Protect against bad actors accessing cloud-native applications
Update and patch systems routinely
Cybercriminals often attack known vulnerabilities in outdated software. Routine updates patch those vulnerabilities.
- Automate system updates for efficiency
- Patch applications, databases, and virtual machines
- Mitigate risks in IaaS and PaaS contexts
Implement a zero trust security model
Zero Trust means "never trust, always verify". No user or system receives open access.
- Continuously verify identity and device health
- Enforce security policies on each login
- Mitigate insider risks with administrative roles as necessary.
Automate security backups and disaster recovery
Data loss occurs as a result of attacks, misconfiguration, or accidents. With backup copy programming, you can begin to recover relatively fast.
- Schedule time to create backup copies for critical data
- Keep a tested incident response plan
- Build your resilience against ransomware attacks and outages
Integrate security into your DevOps pipeline
Security cannot be an afterthought. If you embed it into your application's development, you'll have a much stronger application.
- Implement DevSecOps practices
- Support and run vulnerability assessment tools within CI/CD pipelines
- Find security flaws early, before your release
Leverage AI and automation for threat detection
Cyberattacks happen too fast for humans to deal with alone—integration of automated AI tools to monitor behavior is essential for a good response action.
- Microsoft Defender for Cloud alerts possible threats
- Microsoft Sentinel allows for an automated incident response
- AI-based systems assist in monitoring and documenting to flag deviations, block malicious actors in real-time response action documentation, etc.
Educate employees about the security fundamentals of the cloud
Technology cannot address every threat—human error still has the highest rate of cause security incidents.
- Educate staff with data security protocols
- How to identify phishing emails
- What types of sensitive content they need to be aware of, and if and how to handle it properly.
Tools and Security Solutions for Cloud Environments
To protect cloud environments, organizations must employ a hybrid of existing controls and those that are cloud native.
- Cloud-native application protection platform (CNAPP): Provides coverage for workloads, containers, and Kubernetes clusters.
- Web Application Firewall (WAF): Protects against bad traffic and web-based exploits.
- Firewall services & DDoS protection: Offered by most cloud providers to protect cloud services against overload attacks.
- Vulnerability assessment tools and management tools: Purpose-built tools designed to identify and remediate vulnerabilities in cloud applications.
- Microsoft Cloud solutions: Microsoft Sentinel, Microsoft Defender for Cloud, and Azure Security tools are end-to-end security controls in the cloud.
- Incident response solution (IRS): Integrated platform solutions that include detection of suspicious activity, forensic analysis, and the ability to conduct an incident response plan.
These types of security tooling and processes enable organizations to secure their data. These security practices protect sensitive data, and also provide compliance to various industries.
AI and Automation in Cloud Security
Modern cloud environments are so big and complex that it is virtually impossible to monitor and respond to events manually. AI and automation enable organizations to respond faster than ever to detect, respond to, and adapt to threats. Organizations can leverage AI-based insights with automated tools to enforce compliance and fortify security in cloud environments.
- AI Threat Detection and Response: AI can detect threats in real time, escalate suspicious activities, and stop malicious actors before they are able to cause any damage.
- Compliance automation in CSPM and SIEM: Tools such as Cloud Security Posture Management (CSPM) and Security Information and Event Management (SIEM) facilitate the enforcement of security policies and the checks of compliance and make audits easier.
- DevSecOps and shifting security left in CI/CD: Embedding vulnerability assessments in CI/CD pipelines embeds security practices into development and builds stronger security practices to reduce risks by the time the application is deployed.
Using AI and automation helps organizations scale their defense, reduce human error, respond to incidents faster, and maintain compliance requirements without stalling innovation.
Conclusion
Cloud security has become mission critical in 2025 - it is no longer optional. With the rise of cloud computing, organizations have more risks from unauthorized access, security breaches, and failing to meet compliance obligations. Protecting sensitive data requires an active strategy that uses a combination of technology, policies, and training. There is really no end-to-end security for your organization if you are not protecting all layers of your cloud environment.
Core security resources the significant market players are recommending include zero trust security models, Cloud Security Posture Management (CSPM), vulnerability management, and automated incident response. Each of these areas lay a foundation for an organization's good defense. There are many useful tools, such as CrowdStrike Falcon Cloud Security to assist in threat monitoring and Microsoft Purview Information Protection to protect sensitive information, which can offset the growing risk levels in cloud security. Engaging in penetration testing at regular intervals will also help identify gaps before bad actors exploit them.
At Build Next Tech, we also help enterprises build secure, compliant, and resilient infrastructures across AWS, Google Cloud, and Microsoft Cloud. With our experience and insight in Azure Security, Kubernetes Security, and enterprise-grade security controls, our integrated solution brings confidence as an infrastructure security platform as cloud risk continues to change. Working together towards the right mixture of security solutions and following some basic and well-established cloud security recommendations and best practices will help your organization remain safe, compliant, and future-ready.
People Also Ask
What are the most common cloud threats in 2025?
Unauthorized access, data breaches, DDoS attacks, and misconfigurations are the most common risks.
How do cloud providers secure data?
Cloud providers like Microsoft, Google, and AWS offer firewall services, encryption, and monitoring. Customers must enforce access management. They must also enforce shared responsibility policies.
Why is access management critical for cloud security?
Access management prevents unauthorized access to sensitive information and ensures users only access what’s required.
What tools help improve cloud security?
What tools help improve cloud security? Key tools include CSPM platforms, CNAPP, Web Application Firewalls, Microsoft Defender for Cloud, and vulnerability assessment tools.





















.webp)
.webp)
.webp)