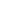OAuth is a common open standard protocol for authorization. It lets applications securely check who users are. It does this without sharing passwords or sensitive information. It lets users give third-party apps limited access to their personal information. This access comes from platforms like Google, Facebook, or Microsoft using access tokens. This method helps keep data safe, secure, and private. Developers need it when they build modern apps and services that require user login and seamless integration with other platforms.
The demand for OAuth-based solutions is growing rapidly across industries. Industry forecasts say the market will reach USD 31.85 billion in 2025. It is projected to grow to USD 105.28 billion by 2035. The compound annual growth rate is 12.7%. More businesses are using OAuth 2.0 authentication today. Enterprises must keep access control management secure.
💡 What is covered in this Blog?
📌 What OAuth is and why it’s important for secure authentication and data access.
📌 An overview of OAuth 2.0 and how it’s different from OAuth 1.0.
📌 How OAuth 2.0 works, including key steps like authorization and access tokens.
📌 Best practices for safely implementing OAuth 2.0 in applications.
📌 Real-world uses and future trends like AI-driven improvements in OAuth.
What Is OAuth Authorization
OAuth is an open standard protocol for authorization. It defines how an application asks a user for permission to access specific resources. It uses access tokens. These tokens are temporary credentials. They show a user's permission without revealing sensitive information.
OAuth includes multiple OAuth flows, such as the authorization code flow, that outline the step-by-step process of requesting and granting access. It supports token authentication. Tokens are exchanged and checked to keep communication secure. The protocol follows rules to protect personal information. It makes sure only authorized applications can access it.
Introduction to OAuth 2.0 Authentication
OAuth 2.0 is a secure authorization protocol that lets users grant limited access without sharing passwords. It uses access tokens to control permissions and supports multiple OAuth flows for web applications, mobile phones, and desktops. It works with JWT authentication. It also manages access control. This helps organizations follow security rules. It helps them meet data privacy laws.
Trusted by platforms like Google APIs and Google Workspace, OAuth 2.0 ensures data security and privacy while enabling seamless user authentication across services.
Importance of OAuth 2.0 for Modern Applications
OAuth 2.0 is important for modern applications. It gives secure, smooth, and efficient user authentication. It also protects sensitive data. OAuth 2.0 helps applications follow data privacy rules. It also makes managing access controls systems easier.
- Secure third-party logins: Enables safe logins like Gmail sign in and Google OAuth integrations.
- Data protection: Safeguards sensitive user information through token authentication.
- Simplified access management: Makes access control management easier across web and mobile platforms.
- Regulatory compliance: Helps organizations meet data privacy services and uphold data and privacy standards.
- Advanced security: Supports two-factor authentication and multi-factor authentication for stronger protection.
- Enhanced user experience: Provides fast, seamless, and trusted OAuth 2.0 authentication workflows.
How OAuth 2.0 Works: Understanding the Workflow Architecture
To understand what is OAuth 2.0, think of it as a secure way for applications to access limited resources on behalf of a user without sharing their password. The OAuth 2.0 protocol focuses on delegating authorization instead of sharing credentials directly. It ensures strong data privacy and security.
.webp)
Here’s how the OAuth flow works step by step, as shown in the diagram:
- Request Authorization
The client (such as a web app) asks the user for permission to access their data. For example, when you choose Gmail account sign in, the app is requesting OAuth permissions through Google OAuth.
# Client Application initiates Authorization Request
endpoint = "https://auth-server.com/authorize"
parameters = {
response_type: "code", # Expect Authorization Code
client_id: "CLIENT_APP_ID", # Unique Client Identifier
redirect_uri: "https://client-app.com/callback",
scope: "profile email", # Permissions requested
state: "random_string_for_csrf" # CSRF protection
}- User Grants or Denies Authorization
The user reviews the consent screen via the Google redirect URL and decides whether to allow or deny access. This step is key to user authentication and helps enforce access control in a security access control system. - Provide Authorization Code
If permission is granted, the authorization server issues a temporary code to the client. This ensures strong authentication and authorization without exposing sensitive credentials. - Exchange Code for Access Token
The client exchanges the authorization code for an OAuth token, typically an access token, which represents delegated rights to fetch protected resources. This is where token authentication and JWT web tokens may be applied for secure verification.
# Step: Exchange Authorization Code for Access Token
POST https://auth-server.com/token
Headers:
Content-Type: application/x-www-form-urlencoded
Body:
grant_type = "authorization_code"
code = "AUTH_CODE_FROM_AUTH_SERVER"
redirect_uri = "https://client-app.com/callback"
client_id = "CLIENT_ID"
client_secret = "CLIENT_SECRET"
# Response from Authorization Server
{
"access_token": "ACCESS_TOKEN_STRING",
"token_type": "Bearer",
"expires_in": 3600,
"refresh_token": "REFRESH_TOKEN_STRING",
"id_token": "JWT_WEB_TOKEN" # if OpenID Connect is used
}- Request Protected Data
With the token, the client can now access the resource server to fetch data (e.g., user profile or email info). This step relies on access control management and can also integrate two-factor or multi-factor authentication to strengthen security.
Key Differences Between OAuth 1.0 and OAuth 2.0
Although OAuth 1.0 offered a way to handle authorization, it was complicated, required cryptographic signatures, and didn’t fully meet the needs of modern applications. With the rise of web applications, mobile phones, and Single Page Apps, along with stricter data privacy regulations, developers needed a more flexible and secure solution.
OAuth 2.0 was introduced to make token authentication easier. It supports multiple OAuth authentication flows. It improves security measures. It ensures compliance with data and privacy standards. It also allows smooth API access delegation and user authentication.
Security Best Practices for OAuth 2.0 Implementation
Ensuring the security of your OAuth workflow is essential to protect user data and maintain trust. Developers can lower risks by following good security practices. This helps make sure that applications using OAuth 2.0 are reliable and follow rules.
Below are the best practices that help secure OAuth implementations across different platforms, like desktop applications and Browser-Based Apps.
- Use a unique OAuth client ID: Register your app in the API Console and assign a distinct OAuth client ID to ensure controlled and monitored access.
- Secure the authorization endpoint: Clearly define and protect the authorization endpoint and authorization request URLs to prevent unauthorized access and phishing attempts.
- Implement token handling securely: Validate and encrypt Token Handling processes, including the access token response, to prevent token theft or misuse.
- Choose safe authorization flows: Avoid using the resource owner password credentials grant, which can expose sensitive data, and opt for safer OAuth 2.0 Flows tailored to your app’s needs.
- Use trusted libraries and APIs: Integrate with Google API Client Libraries and services like Google Drive API to follow industry standards and ensure data protection.
- Understand roles and permissions: Define OAuth 2.0 Roles clearly and use authorization codes appropriately to control user access levels.
- Protect application programming interfaces: Secure application programming interfaces by monitoring API requests and ensuring that only verified interactions are allowed.
Practical Applications of OAuth 2.0 in Modern Development
OAuth 2.0 is widely used to provide secure authorization and seamless access across devices, web applications, and enterprise systems. Here are three real-world scenarios showing its practical applications:
1. Device Authorization Flow: Smart Devices and IoT
Smart devices and IoT gadgets with limited input use OAuth 2.0 for secure login. The device shows a unique code and directs the user to a browser URL (authorization request URL). The user logs in, enters the code, and the authorization server validates it. The device then receives an access token response to access the user’s account without requiring a password.
- The device gains secure access to the user’s account.
- Users avoid entering passwords on devices with limited input.
- Data security and privacy are maintained throughout the OAuth workflow.
- Supports secure Token Handling and proper OAuth client ID validation for each device.
2. Single Sign-On (SSO) Integration for Enterprises
Enterprises implement OAuth 2.0 for SSO so employees can access multiple applications with one login. Users authenticate with a central identity provider (like Google Workspace), which issues access tokens. Each application checks the token before it allows access. This stops users from entering their credentials repeatedly.
- Employees can securely access multiple apps with a single login.
- Reduces password fatigue and improves user experience.
- Administrators manage access centrally, enhancing overall security.
- Works with Browser-Based Apps and application programming interfaces (APIs) for seamless integration.
3. Authorization Code Flow: Web Applications
Web applications use OAuth 2.0 to let users securely log in using third-party accounts (like Gmail). The app redirects the user to the authorization endpoint. The user logs in and grants permission. The server sends an authorization code to the app, which exchanges it for an access token to access user data.
- Users can log in securely without sharing passwords.
- Applications receive access tokens to interact with the Google Drive API and other Google API Client Libraries safely.
- Supports advanced OAuth 2.0 authorization and OAuth 2.0 Roles, maintaining strong access control management.
Future Trends and Innovations in OAuth 2.0
OAuth 2.0 is continuously evolving to meet the growing demands of secure user authentication and access control. New standards and improvements are making it easier for developers to implement safe and seamless login experiences across platforms.
Key trends and innovations include:
- OAuth 2.1 Adoption: Simplifies OAuth flows, removes outdated methods, and strengthens token handling for better security.
- Enhanced Single Sign-On (SSO) & Social Login: Users can access multiple apps with one login, improving convenience and reducing password fatigue.
- Advanced Multi-Factor Authentication (MFA): Combines passwords with additional verification methods, increasing protection for web and mobile applications.

- Stronger Access Control Management: Enterprises can enforce precise permissions, keeping sensitive data safe across APIs and cloud services.
- Better IoT & Browser-Based App Support: Devices with limited input and browser-based applications can integrate OAuth securely, making workflows smoother.
Conclusion: Key Insights and Takeaways About OAuth 2.0
OAuth 2.0 is a modern, secure protocol that allows applications to authorize users without sharing passwords. It provides a safe way to manage access. It ensures data privacy and security. It also offers smooth login experiences across web, mobile, and enterprise platforms. Developers and businesses increasingly rely on OAuth 2.0 to implement strong access control management.
The protocol supports multiple OAuth flows. These include device authorization, SSO, and authorization code flow. This makes it adaptable for different real-world scenarios. With the growing use of APIs, IoT devices, and browser-based apps, OAuth 2.0 remains the industry standard for secure authentication and seamless integration across systems.
BuildNexTech is a software development company in Hyderabad offering software development services and also web development services. It also provides cloud DevOps services, data migration services, and AI development services to support businesses. The company delivers customized solutions to streamline operations, boost productivity, and foster innovation. With a skilled team, BuildNexTech ensures high-quality, timely, and scalable development that meets the evolving needs of modern businesses.
People Also Ask
What is the difference between IMAP and OAuth?
IMAP is a protocol for accessing email, while OAuth is an authorization framework that securely grants limited access without sharing passwords.
Why is password grant deprecated?
The password grant exposes user credentials and lacks strong security, making it vulnerable; hence, safer flows like authorization code are recommended.
Is OAuth more secure than JWT?
OAuth is a framework for access delegation, while JWT is a token format; OAuth with JWT can be secure, but OAuth’s overall security depends on implementation.
Does OAuth 2.0 support SAML?
OAuth 2.0 and SAML are separate protocols, but they can be integrated for authentication and authorization in federated identity systems.















.webp)





.webp)
.webp)
.webp)