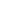In 2025, data powers everything from AI-driven innovation to cloud computing. Still, it also brings unprecedented security challenges, especially with evolving cyber threats, stricter data security compliance, and global cloud data security challenges. For security engineers and CS enthusiasts, mastering data masking (or obfuscation) and data encryption is no longer optional; it’s essential.
These tools protect sensitive information differently, and knowing when to use each is key to building a secure, compliant system. This guide breaks down both approaches, explores emerging trends like quantum computing and privacy-protected AI development, and offers practical strategies for safeguarding data in an increasingly connected and regulated world.
💡 What’s Next? Keep Scrolling to Discover:
🚀 How top cybersecurity teams combine data masking and encryption for ultimate protection
🚀 The emerging role of AI-powered tools in privacy-protected AI development
🚀 Secrets to securing cross-border data transfers in cloud-first environments
🚀 How global security teams use Security Information and Event Management (SIEM) for real-time monitoring
🚀 Essential skills and certifications to excel in the future of data security
Introduction: Understanding Modern Data Security Needs
In today’s digital-first world, protecting sensitive data is no longer optional; it’s a necessity. From enterprises to startups, data security compliance is crucial, driven by rising cyber threats, stringent privacy regulations such as GDPR and HIPAA, and the growth of cloud computing, which presents new data security challenges.
Two prominent strategies in modern cybersecurity are data obfuscation (masking) and data encryption. While both protect sensitive information, they serve different purposes and operate in unique ways. Choosing the right approach often depends on the data environment, regulatory requirements, and the organization’s risk tolerance.
Key reasons for prioritizing data protection in 2025:
- Escalating incidents of data breaches affecting millions of users
- Growing reliance on cloud-based environments, making cloud data security challenges more prominent
- Stricter compliance requirements for data protection officers and cybersecurity teams
- The need for robust safeguards in software development and production systems
- Increasing demand for secure data collaboration across organizations and offshore partners
By understanding the distinctions between dynamic data masking, static data masking, fidelity-preserving encryption, and other emerging methods, security engineers and CS enthusiasts can better architect secure systems.
What Is Data Masking in Cybersecurity and Why It Matters
Data masking is a vital technique in modern security. This answers the question “what is data masking?” in cyber security, which is increasingly important for compliance. This ensures that sensitive data, such as personally identifiable information (PII), financial records, or health records, is hidden from unauthorized users while still retaining its usefulness for legitimate purposes like testing, development, and analysis.
Definition of Data Masking and Real-World Examples
Data obfuscation is a technique that alters sensitive information so that unauthorized users cannot access the real values, while preserving its usability for testing, analytics, or development purposes. It works by replacing actual data with fictitious but realistic equivalents.
Examples of obfuscation:
- Masking credit card numbers for fraud detection models while analyzing transaction patterns
- Redacting personal identifiable information (PII) in medical records for Privacy Protected AI Development
- Applying Microsoft Purview masking features to data shared with third-party developers in secure collaborative environments
These are common data masking examples applied in real-world cybersecurity.
This approach is especially relevant for sectors such as healthcare providers, finance, and large-scale AI-powered research projects where sensitive data is processed.
Key Benefits of Data Masking for Businesses
Data obfuscation offers several advantages:
- Compliance assurance: Meets HIPAA security rules and PCI DSS 4.0 requirements for secure handling of sensitive data
- Fraud prevention: Enables testing of fraud detection models without exposing actual transaction data
- Safe data collaboration: Supports secure federated analytics and secure collaborative AI projects
- Operational efficiency: Provides realistic datasets for development without jeopardizing security
These benefits make data obfuscation best practices essential for enterprise cybersecurity in 2025.
Best Practices for Data Masking Implementation
Implementing obfuscation effectively requires:
- Leveraging data discovery & classification tools to identify sensitive datasets
- Applying masking policies that align with compliance and operational needs
- Using static data masking for development/testing and dynamic data masking for real-time environments
- Ensuring encrypted queries during cross-border data transfers for offshore partners
- Incorporating continuous monitoring through Security Information and Event Management systems
By following data masking best practices, such as using SQL Server data masking or data masking SQL Server features, ensure strong protection at the database layer.
What Is Data Encryption and Why Is It Essential
Data encryption is a fundamental cybersecurity technique that protects information by converting it from a readable format (plaintext) into an unreadable format (ciphertext). This transformation ensures that sensitive data remains inaccessible to unauthorized parties, even if intercepted during transmission or compromised at rest.
Access to encrypted data requires a decryption key, a secure credential known only to authorized users or systems. This highlights the question “why is encryption important?” in ensuring both data security and data privacy.

Types of Encryption Algorithms You Should Know
Data encryption transforms readable data into unreadable ciphertext that can only be accessed by authorized users with the correct key. Encryption is essential for Office 365 data security, secure storage, and encrypted data transfer.
Key algorithms include:
- DES algorithm (Data Encryption Standard): A symmetric method largely replaced due to vulnerability to brute-force attacks
- AES (Advanced Encryption Standard): Offers 128 bit encryption or higher for robust protection
- RSA encryption: Uses asymmetric keys for secure communications
- Fidelity-preserving encryption (FPE): Protects sensitive data while maintaining its original format for usability in production
- Homomorphic encryption: Enables computations on encrypted data, critical for privacy-protected AI development and cloud-based analytics
Understanding these encryption types is critical for robust data center security.
Practical Use Cases of Data Encryption Across Industries
Encryption is applied in varied contexts:
- Healthcare: Protecting electronic medical records for HIPAA compliance
- Finance: Securing transactions to meet PCI DSS 4.0 and fraud prevention requirements
- Cloud Computing: Protecting cross-border data transfers
- Corporate Collaboration: Using secured datasets for AI research without exposing sensitive content
- Government & Defense: Supporting zero footprint investigations for critical data
Encryption ensures not only security but also regulatory compliance in every industry.
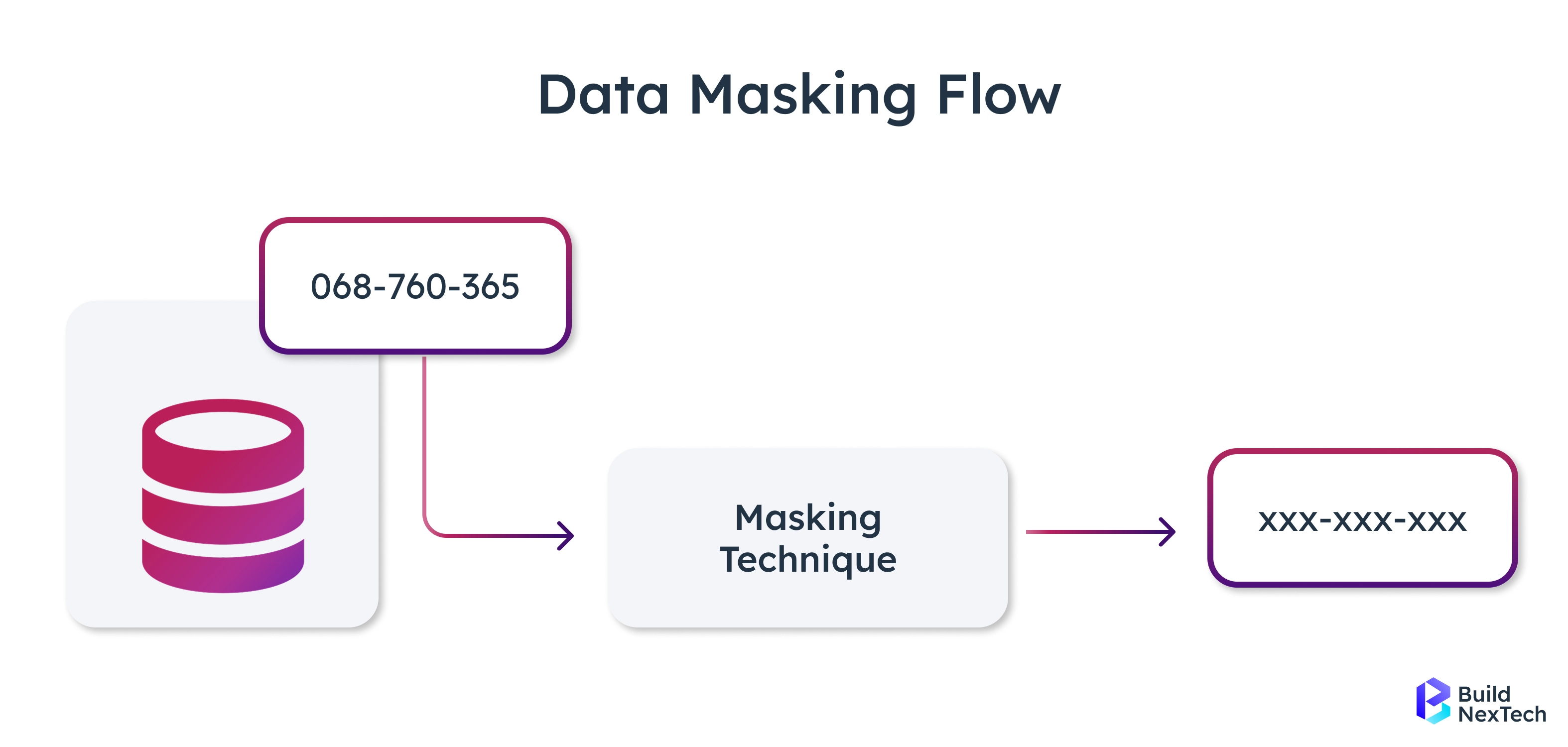
Comparing Data Masking vs. Data Encryption in Real-World Scenarios
In today’s cybersecurity landscape, protecting sensitive data requires a multi-layered approach. Two of the most widely adopted techniques, data masking and data encryption, serve distinct purposes and are applied differently depending on the security requirements of a system. While both aim to protect sensitive information, understanding their differences is critical for selecting the right approach for a given scenario.
Key Differences Between Masking and Encryption
Understanding these differences supports cybersecurity compliance and is often recommended by top data security companies and leading cybersecurity firms.
Choosing the Right Approach for Compliance
For organizations with compliance obligations, a hybrid strategy is ideal:
- Dynamic data masking for live systems and analytics
- Encryption for data at rest and in transit
- Use secure federated analytics and secure query processes for collaborative projects
- Ensure data protection officers oversee compliance and security measures
This layered approach addresses both data privacy regulations and real-world security risks.
Case Study – Capital One Databolt Data Security Solution
Capital One’s Databolt solution combines obfuscation and encryption to safeguard sensitive data.
- Challenge: Protect customer data in development environments without slowing analytics
- Solution: Applied dynamic obfuscation with AES encryption for data at rest and encrypted queries in cloud environments
- Outcome: Reduced breach risk, enabled secure data collaboration, and improved regulatory compliance
This case illustrates the power of a combined approach for modern enterprises.
Future Trends in Data Security
As data continues to grow exponentially in volume, variety, and value, safeguarding it is becoming increasingly complex. The future of data security will not only rely on traditional techniques like data masking and encryption but will also integrate advanced, adaptive approaches designed to address emerging cyber threats and evolving regulatory requirements.
The coming years will see significant innovation driven by advances in artificial intelligence, quantum technologies, cloud computing and data security. These innovations will fundamentally change how organizations secure sensitive data, enabling more intelligent, efficient, and privacy-conscious data protection methods.
Emerging Methods and Tactics in Data Masking & Encryption
The future of data protection will feature:
- Privacy-protected AI development through synthetic data generation
- Secure collaborative AI using masked and encrypted datasets
- Adoption of fidelity-preserving encryption for sensitive analytics
- Use of quantum computing to develop unbreakable encryption protocols
These innovations will shape how enterprises handle sensitive data securely.
Cybersecurity Certifications and Principles to Master
Security professionals should pursue:
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- Courses in cybersecurity principles and security information and event management
- Mastery of secure federated analytics and data privacy regulations
These certifications are essential for advancing in cybersecurity roles.
Future of Data Security in Cloud and AI
As organizations adopt cloud-first strategies, future security trends include:
- Encryption-driven data security in multi-cloud environments
- AI-powered data discovery & classification tools
- Advanced user behavior analytics to detect threats
- Adoption of zero trust frameworks for cross-domain investigations
These advancements will define the future of cybersecurity.
Step-by-Step: Protecting a Use Case with Data Masking and Encryption
Implementing a robust data protection strategy requires a structured approach that combines both data masking and encryption, tailored to the specific needs of your use case. By following a step-by-step methodology, organizations can ensure that sensitive information is safeguarded while maintaining the usability of data for legitimate purposes such as testing, analytics, and AI development.
Data discovery tools should support compliance. Oversight often falls to a data protection officer (DPO). Addressing questions like “What is a data protection officer?”, “What does a data protection officer do?” and “What is the main task of data protection officers?” help organizations assign responsibility effectively.
Identifying Sensitive Data Within the Use Case
Begin by identifying:
- PII such as names, addresses, and Social Security numbers
- Payment details for fraud detection models
- Proprietary datasets for AI-powered research
- Sensitive logs from security cameras and IT infrastructure
Data discovery tools should support compliance and security information and event management.
Applying Masking and Encryption in the Right Stages
- Use static masking for stored datasets
- Apply dynamic masking for real-time queries
- Encrypt sensitive datasets at rest and in transit
- Maintain role-based access control for offshore partners and third-party developers
This ensures secure data collaboration while maintaining compliance.
Monitoring, Testing, and Continuous Improvement
Security is an ongoing process:
- Monitor via security information and event management (SIEM) tools
- Test masking/encryption methods regularly
- Incorporate feedback for continuous improvement
Continuous improvement builds stronger defenses and aligns with cybersecurity awareness month initiatives. Many professionals pursue a cybersecurity certificate to gain expertise in encryption, masking, and SIEM tools.
Final Thoughts
Data masking is a vital technique in modern security. This answers the question ‘what is data masking in cyber security’, which is increasingly important for compliance. In 2025, protecting sensitive data requires more than just one defense; it demands a layered strategy. Organizations are combining data masking, DES encryption, modern ciphers, and strong governance practices to protect critical information. Encryption remains central to security, whether through advanced encryption code implementations or enterprise adoption of solutions that explain “Why use encryption software?” is essential for secure operations.
At the same time, compliance plays a critical role. From GDPR to healthcare, where the HIPAA security rule applies to data contained in electronic records, businesses must align with strict regulations. This is where cybersecurity compliance frameworks and audits provide confidence to regulators, customers, and partners.
To stay ahead of threats, companies increasingly partner with top data security companies, top cybersecurity companies, and innovative cybersecurity firms that drive new approaches in AI-powered protection, cloud resilience, and zero-trust frameworks. Ultimately, success in modern security is about achieving balance, ensuring both data security and data privacy while adapting to an evolving digital landscape.
People Also Ask
Is masking a form of encryption?
No. Masking (data obfuscation) hides sensitive data by replacing real values with fake but realistic ones, mainly for testing or analytics. Encryption, however, secures data through a reversible cryptographic process that can only be undone with a valid key.
What is another name for data masking?
Data masking is also called data obfuscation or data anonymization, as it conceals real data to prevent exposure while preserving its structure.
What is the difference between data hiding and data masking?
Data hiding restricts access to information through permissions or access controls. Masking, on the other hand, transforms the data itself so that even if accessed, it doesn’t reveal sensitive information.
What is the most secure encryption?
AES-256 is widely recognized as one of the most secure encryption standards due to its strong 256-bit key length. Some specialized systems also use fidelity-preserving encryption.




















.webp)
.webp)
.webp)